Email impersonation
cyber threat protection
91% of all cyber attacks use email as #1 attack vector.
Email impersonation is currently the top cyber threat all kinds of organisations must deal with.
We protect all kinds of email communications
from all cyber attacks providing
a simple and interpretation free verdict
on every email in your inbox

How can we protect you and your business from email Fraud?
Zuratrust is an independent verification channel, based on the same principle second factor authentication relies on. Allows the verification of all your email communications in a plain easy and systematizable manner. Once you know which emails are trustworthy, email fraud is gone.
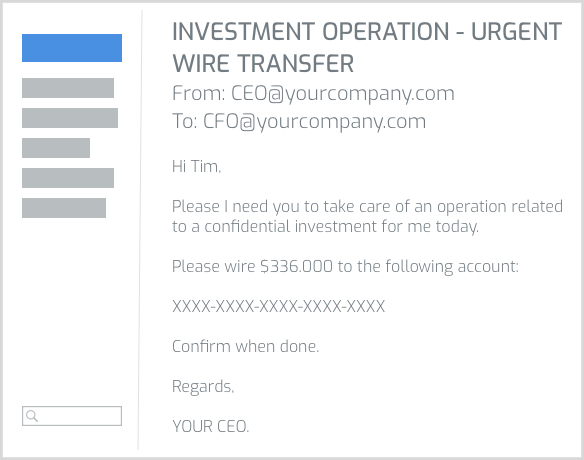
EMAIL COMMUNICATIONS
ARE YOUR BIGGEST CYBER RISK
91% of all cyber attacks use impersonated emails as the number one attack vector, and our human resources are not ready to face this threat that might cause feaar and decision blockage in their everyday tasks.
We all need a decision tool that fits in our daily work that will help us discriminating real emails from cyber attacks.
Is your organisation ready to face this?
Request a Demo
A solution for each email communication
Whether you are sending a regular email to a customer, contractor, bank representative, colleague or managing automatic emails sent from any of your business management applications to third parties, we've got you covered.
- CEO Fraud, BEC, Ransomware, Intelectual property theft,... protection
- Compatible with 100% of corporate and personal email platforms (self hosted, cloud, ...)
- Protects emails sent and received on all kinds of devices and Operating Systems
- No changes needed in corporate email infrastructure (Zero setup)
- Protection all email related attacks (also targeted, unique and complex attacks)
- Instant email verification
- Emails sent and received within the company or to any 3rd party
- ... your recipients can be sure your emails are real.
- Protection for Outbound Phishing attacks
- Works with all kinds of email sending plaforms (on-premise, SaaS, ...)
- Protects emails received on all kinds of devices and Operating Systems
- Rule-based automatic outgoing email protection
- Protect your brand and your customers
- Protection all email related attacks (also targeted, unique and complex attacks)
- Instant email verification
- Any email source: CRM, ERP, newsletters, invoicing, payments, intranets, project management, transactional or non transactional,...
- ... your recipients can be sure your emails are real.

DKIM, SPF AND DMARC
ARE VERY IMPORTANT,
BUT NOT ENOUGH
This security measures are very important to protect your outgoing emails and to make email spoofing on your domains more difficult.
Anyway current cyber gangs invest big money in attacks and can easily bypass this basic protection measures.
Request a Demo
Why should I protect my email
communications with Zuratrust?